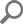Applies to
ApexSQL Audit 2020.03 and higher
Summary
This article describes how to configure sensitive data classification and auditing in ApexSQL Audit
Description
In this article we are going to demonstrate how to easily configure auditing for sensitive data access, configure and apply data classification rules, and how to utilize on custom or built-in search criteria for sensitive data in MS SQL databases.
Discovery of sensitive information in a database, and how the data search is being performed come before the auditing implementation. The next chapter explains how to identify the sensitive data within the database via pre-define and custom rules.
Knowing where the sensitive information is stored in your organization is first step in creating sound security strategy. Sensitive data discovery within ApexSQL Audit brings 50+ pre-defined rules divided in several categories
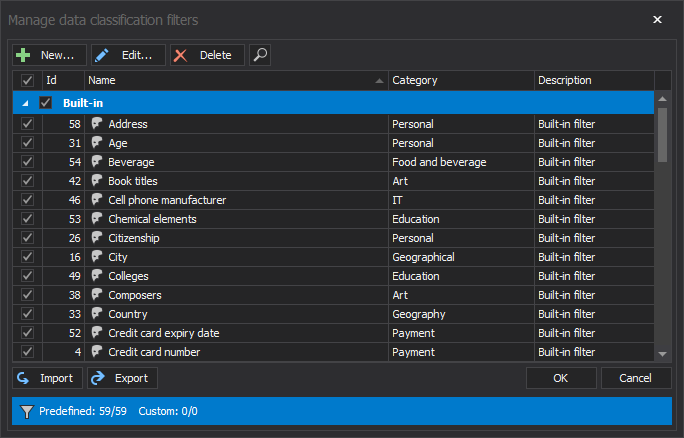
The search criteria can be expanded via specifying the custom set of rules that will be used as a base to determine sensitive information in a database. To create and apply custom rules set it takes several steps:
- Go to Configure tab in the ApexSQL Audit main application ribbon
- Highlight the audited database and head to Sensitive columns configuration set
-
Choose the Criteria button to open data classification management window and click New
-
In the Add filter dialog, custom filters are specified via:
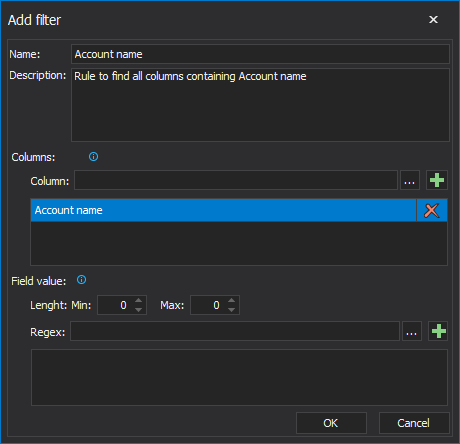
- Filter name
- Description
- Filtering by the column name
- Filtering by the field length
- Filtering by data via Regex expression
To learn more about sensitive classification filter management and options, visit this Sensitive data classification article
-
Once the rule is created, it is shown in the custom filters list and can be enabled by tickling the checkbox in the grid
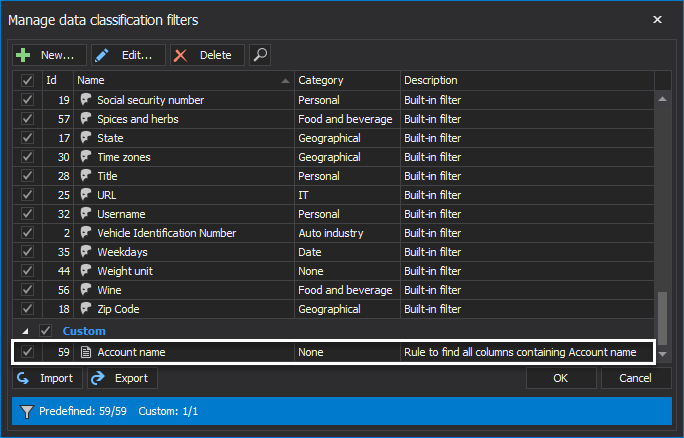
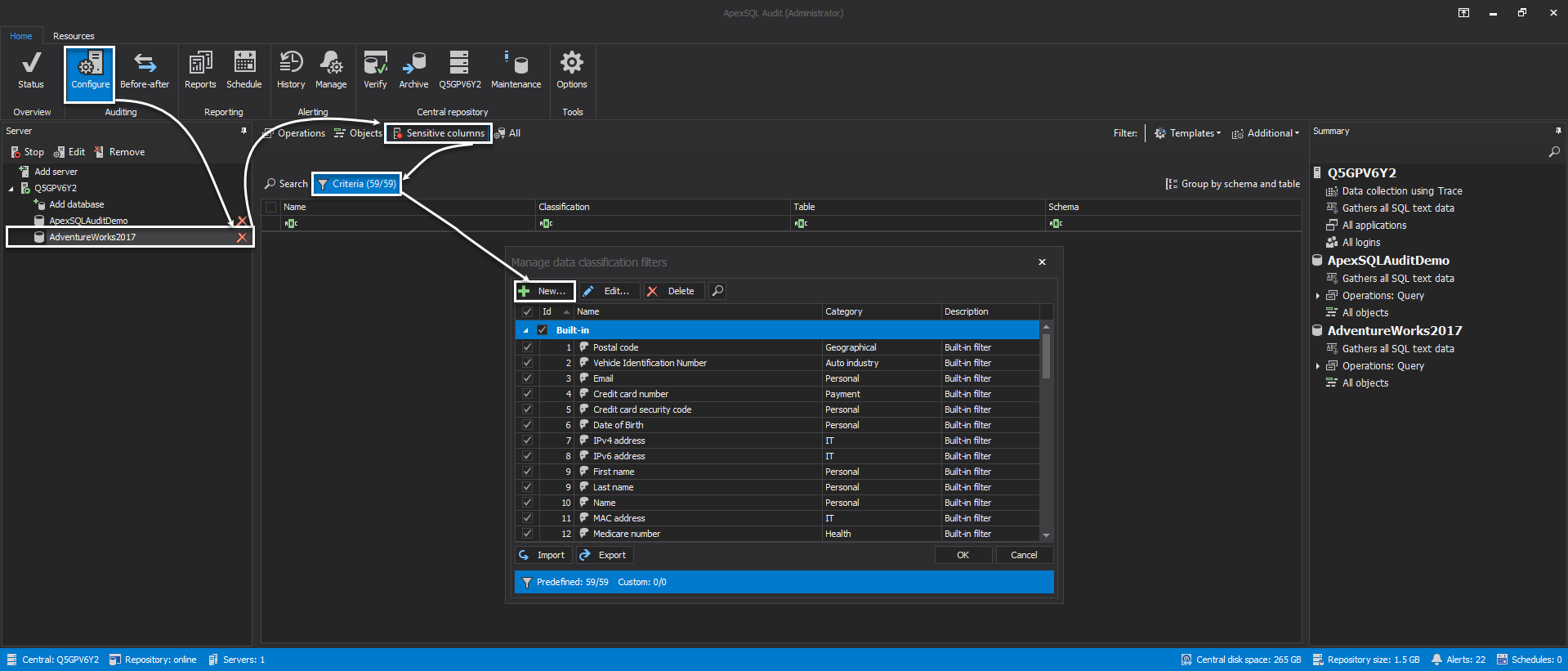
After the rules are created, and list of rules is finite for the sensitive columns search, the auditing configuration can be done quickly. Sensitive data access auditing starts with the sensitive columns discovery by clicking the Search button.
Once the search is initiated, the grid is automatically populated with the columns that match the search criteria and are flagged for auditing with additional graphical indicator with the red circle in the bottom-right corner of the column icon ![]() .
.
The sensitive column list can be customized to either include or exclude any input from it by tickling the check-boxes in the grid. The configuration is complete by choosing the Apply button in the configuration change ribbon

All configuration details including sensitive columns list can be quickly reviewed in the Summary pane
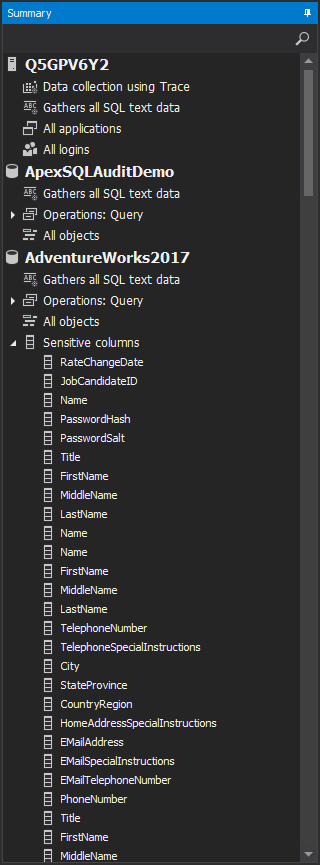
With that, the configuration for sensitive data access is complete, to learn more about how to extract reports and configure alerts for sensitive data auditing, please visit this Creating sensitive data reports and alerts article.