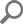Applies to
Summary
This article explains how to link a database to a Git repository using the SSH protocol generated by Command Prompt or GitBash.
Description
ApexSQL Source Control natively supports different protocols that can be used to connect to a Git repository. This includes HTTP, HTTPS, File, and SSH protocols. In this article, we‘ll go through the process of generating a key pair using Command Prompt and GitBash and linking a database using the SSH protocol.
Command Prompt
To generate the SSH keys, open Command Prompt, and type in ssh-keygen. The result will be:
Generating public/private rsa key pair.
Enter file in which to save the key (C:\Users\<username>/.ssh/id_rsa):
Hit the Enter keyboard key to verify the creation of the default SSH key and path for storing the SSH keys. The next step is to define the passphrase and confirm it by re-entering it again:
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Hit again the Enter keyboard key to create the default identity with public and private SSH keys. This will be the result:
Your identification has been saved in C:\Users\<username>/.ssh/id_rsa.
Your public key has been saved in C:\Users\<username>/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:Bs6nRUN4SJVJT9UGhWFbvPc
GitBash
If the GitBash is used for creating the SSH keys, the following command should be typed in ssh-keygen -m PEM. The rest of the creating SSH keys process after that is completely the same as already explained under the Command Prompt section.
After the SSH keys are generated, open the id_rsa.pub file as a text file, copy it, and store it in the source control repository.
Now, for linking a database to the repository, under the System login tab, the SSH tab will be chosen and an SSH URL will be used:
FAQs
Q: What is SSH?
A: SSH or Secure Shell is an encrypted network protocol used for secure communication over the internet.
Q: What source control systems is it used with?
A: ApexSQL Source Control supports SSH connections for Mercurial, Git, and Subversion.
Q: What is the main advantage of SSH protocol?
A: Data sent via SSH is strongly encrypted and thus less susceptible to attacks.